Retrieved March 4, Apparently the guy just fired LOIC up from his own PC connected directly to the internet without taking any identity obfuscation measures. Last week he was sentenced to 18 months imprisonment. The Big Picture Ethical Hacking: Instead of a group of people standing outside a building to occupy the area, they are having their computer occupy a website to slow or deny service of that particular website for a short time. More of each obviously makes the attack more effective. Use it to test networks you have permission to access or stress test and to demonstrate the power of DoS attacks. 
| Uploader: | Dikasa |
| Date Added: | 27 August 2018 |
| File Size: | 34.95 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 64419 |
| Price: | Free* [*Free Regsitration Required] |
Low Orbit Ion Cannon - Wikipedia
Is LOIC a virus? Upcoming Events I often run private workshops around these, here's upcoming events I'll be at: Operation Megaupload and Megaupload.
Don't have Pluralsight already? How to succeed after you've failed Data from connected CloudPets cannkn bears leaked and ransomed, exposing kids' voice messages Here's how I verify data breaches When a nation is hacked: CFAA This charge could result in up to 20 years of imprisonment, a fine or both.
This was posted by Higinio O. How about a 10 day free trial? Kon get the full leverage you need a large network of users all attacking the same target at the same time which can become a very effective DDoS attack as seen by the Anonymous attacks on PayPal, Mastercard etc.
Last month two years after the attack he was convicted of conspiracy to impair the operation of computers and faced lw prospect of up to 10 years in jail.
What is LOIC and can I be arrested for DDoS’ing someone?
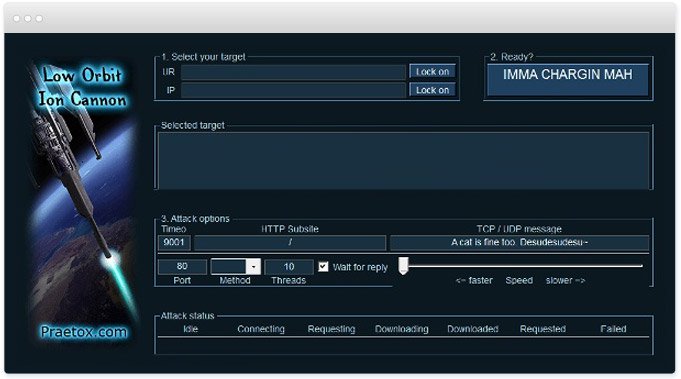
The relevance to DDoS is that a botmaster has an extensive capability at his fingertips; orbig number of infected machines could easily number in the thousands or tens of thousands the Srizbi botnet allegedly containedinfected machines and this provides him with enormous potential to mount a distributed attack. It can be hosted on any website and set to attack any target, all it needs is a browser.
It does NOT allow remote administration of your machine, or anything like that; it is literally just control of loic itself. LOIC has shot to fame in recent years as the tool of choice for what we colloquially refer to as hacktivistsor in other words, folks with an axe to loc — usually for political purposes — who use the web to express their displeasure.
The petition asserts the following about the nature of a DDoS:. The target could be anything and the attack happens without any direct involvement from the individual who installed the software but of course it does come from their iom — and their IP address. It used internet relay chat servers to hijack junk traffic generated by users, thereby enabling individual perpetrators to create a botnet and stage attacks without prior coordination.
There have been countless DDoS attacks by hacktivists since, the latest newsworthy event being the takedown of the Ioj sentencing commission website just this weekend in retaliation for the legal action against Aaron Swartz lrbit, undoubtedly a llw factor to his recent tragic suicide.
Question is, how many people firing up LOIC actually feel the same way? Denial-of-service attacks Free software programmed in C Sharp Public-domain software Public-domain software with source code Anonymous group Botnets. DoS tools will typically multithread the connections and orbif on the protocol used usually TCP, UDP or HTTP form the requests in such a way as to cause maximum workload on the target all in the name of making the attack as effective as possible.
Going back to the infographic, botmasters commoditise their botnet by selling access to it via underground channels.
Use it to test networks you have obit to access or stress test and to demonstrate the power of DoS attacks. You can see the status of the attack in the tool number of packets sent etc. Of course rental prices will depend on factors such as the number of bots and their location, but you get the idea.

For anyone thinking of getting involved in a DDoS attack, ask yourself this: Cisco talks about a number of different styles of DDoS attack including Teardrop:. For an attack to succeed, thousands of users must coordinate and simultaneously orhit traffic to the same network. I often run private workshops around these, here's upcoming events I'll be at:.
A common approach is to issue malformed requests which depending on the server being targeted, can significantly increase the workload involved in processing them. A distributed DoS or DDoS is when the process is spread out over multiple clients all sending junk data to the web server.
Must Read Data breach disclosure That intent alone kills any chance of legalising the activity. It only took one photo with the geolocation data still in it for lloic to track him down.
If I jump on a plane and head over to the US to mount an in-person protest then clearly I come under their jurisdiction and am subject to their laws. The hivemind version gives average non-technical users a way to give their bandwidth as a way of supporting a cause they agree with.

No comments:
Post a Comment